I played a bit with influxdb version 2.0.0, telegraf client and two of my raspberry pies.
On my oldest pi a 1 B+ the telegraf client caused too much performance issues on that light weight single CPU and 480 MB of usable RAM. So I chose a simple bash script with curl to send the CPU temperature to influxdb.
#!/bin/bash
timestamp=$(date +%s)
temp=$(vcgencmd measure_temp)
curl -XPOST \
"https://flux.example.com/api/v2/write?org=none&bucket=pihole&precision=s" \
--header "Authorization: Token asas==" \
--data-raw "cpu-temperature,host=pihole ${temp//\'C/} ${timestamp}"
At first I was running influxdbd by hand. But I didn’t want the usual port of 9999 of the alpha version and I also wanted SSL encryption when I log into the backend. Pretty easy with the already running apache on that server.
<VirtualHost *:443>
ServerName flux.example.com
DocumentRoot /var/www/empty
<Directory /var/www/empty>
Options Indexes FollowSymLinks
AllowOverride None
Require all granted
</Directory>
ProxyPass / http://localhost:9999/
ProxyPassReverse / http://localhost:9999/
SSLEngine on
SSLCertificateFile fullchain.pem
SSLCertificateKeyFile privkey.pem
</VirtualHost>
so far so good. Starting the influxdb by hand after a reboot or failing isn’t an option. So I created by on systemd service file
sudo $EDITOR /lib/systemd/system/influxdb2.service
[Unit]
Description=InfluxDB 2.0 service file.
Documentation=https://v2.docs.influxdata.com/v2.0/get-started/
After=network-online.target
[Service]
User=influx
Group=influx
ExecStart=/usr/local/bin/influxd
Restart=on-failure
[Install]
WantedBy=multi-user.target
Do not forget to enable it :D sudo systemctl enable influxdb2
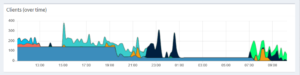
So far I made one observation. The telegraf client is doing a lot of DNS requests through the network. If I’m not wrong it does it for every request. If you look at the graphic you see that the bottom a big blue line. That is the DNS requests from telegraf. At some point around 20:00 You see a drop. Well there I change the flush interval to 120 seconds. Later at round 7:30 I wrote the IP and host name into /etc/hosts and the “noise” was gone. That is something you maybe want to do in your devices, too to save some bandwidth and energy.